Sign up for a live no-commitment demonstration of RansomCare today! Or, chat with a sales representative.
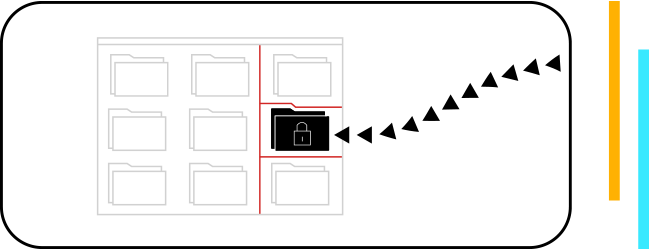
ongoing encryption and file corruption on monitored devices, instantly raising an alert to breaches. All activity is displayed on a dashboard in real time so you can witness the near-immediate response to any attack as it happens.
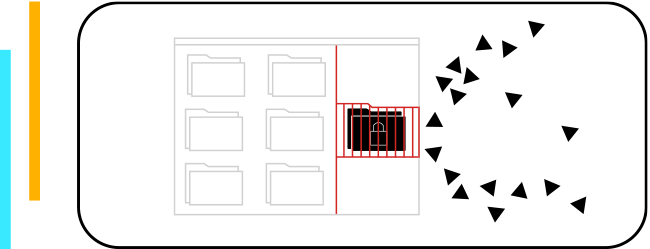
automatically to stop the threat in seconds by disabling and isolating the device and user encrypting your data. It also notifies those who need to know what’s happening.
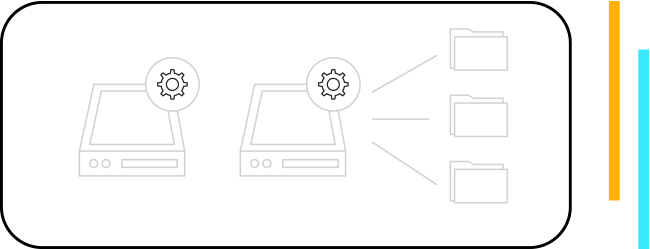
an exact list of the few encrypted files before the forced shutdown for easy document recovery and minimal downtime to the network or infected computer.

both internal and external information to maintain compliance regulations and keep things running smoothly.
RansomCare adds a vital protective layer to your data, complementing your existing security stack.